🚀 Passionate Cybersecurity Professional & Tech Enthusiast 🚀
Greetings! I'm Daniel Rajaram, a tech enthusiast and dedicated graduate student pursuing a Master's in Cybersecurity at New York University. With a solid foundation in IT and Cybersecurity, my educational journey began at the New Jersey Institute of Technology, where I graduated with honors in IT and CS.
🌐 Professional Experience: 🌐
🔍 Legend Biotech - Data Governance Intern:
Led a transformative data mapping automation project, enhancing data cataloging and classification. Collaborated globally using tools like One Trust and Excel, emphasizing the pivotal role of cybersecurity in the digital landscape.
💼 AustinCSI - Management Consulting Intern:
Crafted and presented a strategy for a new client, gaining proficiency in Microsoft Power Apps, Power Automate, SharePoint, and Forms for process automation. Developed analytical acumen, leadership, and collaboration skills in a diverse professional environment.
🎓 Education: 🎓

Master's in Cybersecurity - New York University:
Actively staying at the forefront of industry advancements, pursuing additional certifications to align with the evolving cybersecurity landscape.

Bachelor's in IT and CS - New Jersey Institute of Technology:
Graduated with honors, laying a strong academic foundation in technology.
📚 Continuous Learning & Certification: 📚
CompTIA Security+


I am officially certified with CompTIA Security+. This certification validates my comprehensive knowledge in IT security, covering essential areas such as threat analysis, incident response, identity management, and risk management. It also demonstrates my expertise in implementing secure network architectures, cryptography, and ensuring compliance with security regulations. With this certification, I am equipped to assess and mitigate vulnerabilities across various environments, helping businesses safeguard their data and systems from emerging threats.
Google in Cybersecurity
Certified by Google in Cybersecurity, I am committed to staying at the forefront of industry advancements. Actively pursuing additional certifications that align with the evolving landscape of cybersecurity to increase my skills and knowledge in this field.
🤝 Passion and Values: 🤝
Fueled by an unwavering passion for technology and a belief in the paramount role of cybersecurity in safeguarding digital landscapes. Guided by principles of respect, integrity, service, excellence, stewardship, collaboration, honesty, fairness, courage, empathy, empowerment, challenge, drive, efficiency, and forward-thinking.
🌟 Mindset: 🌟
Thriving in teamwork and project endeavors, I aim to contribute to organizational growth and success by leveraging my skills and knowledge.
#ProblemSolving #Communication #Adaptability #AnalyticalThinking #TimeManagement #ProjectManagement #IncidentResponse #EncryptionTechnologies #FirewallManagement #SIEM #CloudSecurity #Programming #RiskManagement #IAM
Github
During my internship at Legend Biotech as a Data Governance Intern, I played a crucial role in utilizing the OneTrust Compliance Tool, which consists of various modules and serves as a compliance tool for the Data Governance Program, Data Privacy Office, Third-Party Risk Management, and more.
In the realm of Data Governance, I extensively worked with modules such as Data Automation, Data Discovery, and Data Catalog within OneTrust. This involved automating the creation and maintenance of data inventories, tracking personal data flow across the organization, ensuring compliance with privacy regulations, and providing insights into data usage and processing. The tool facilitated risk assessment and informed decision-making.
A significant aspect of my responsibilities included managing the Record of Processing Activities (ROPA), which involved gathering information to populate data inventories, enabling customized assessment templates, and automating data collection for mapping. This was essential for comprehensive data tracking.
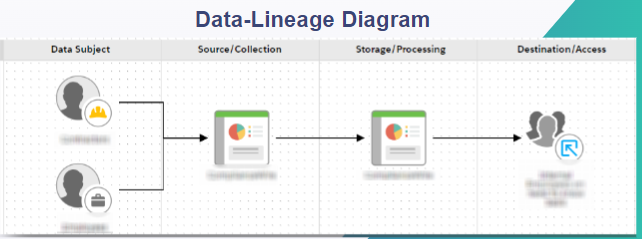
I also engaged in the visualization of the journey of data throughout Legend Biotech, tracking how data moves, transforms, and interacts with different systems. This not only enhanced transparency and access but also provided insights into the data lifecycle and compliance implications.
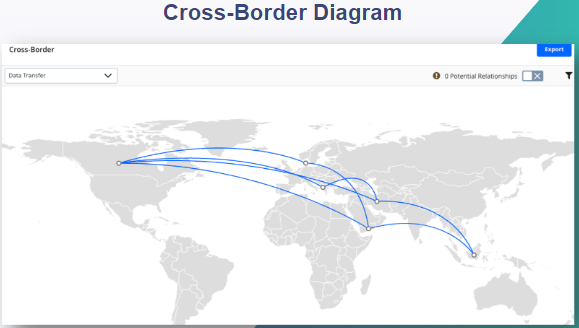
My role extended to addressing complexities of international data transfers, ensuring compliance with data protection laws across borders, and tracking the movement of data between different jurisdictions. This involved assessing and mitigating cross-border data risks and contributing to the development of a global privacy strategy.
In collaboration with global teams, I gained a comprehensive understanding not only of Legend Biotech's Data Governance Program. but the entire biotech company as a whole. I worked closely with various IT functions and business units, supporting day-to-day activities and project initiatives. I learned and implemented industry best practices for data governance, including data cataloging, mapping, and classification, utilizing tools like OneTrust and Excel.
Key Skills: Data Mapping, Data Automation, Microsoft Excel, Microsoft Power BI, Presentation Skills, Teamwork, Good Documentation Practice (GDP), Good Manufacturing Practice (GMP), Data Analysis, Organization Skills, Time Management, Attention to Detail, Communication.
Overall, my internship provided me with a wealth of experience in data governance processes, tools, and best practices, enhancing my skills in data management and compliance.
PwC Switzerland Cybersecurity Job Simulation (August 2024) I participated in a job simulation with PwC Digital Intelligence, focusing on integrated defense strategies. I developed a deep understanding of these strategies and their application in real-world scenarios. My tasks included conducting risk assessments and formulating security recommendations. I demonstrated proficiency in cybersecurity terminology, network segmentation, and firewall configuration.
Mastercard Cybersecurity Virtual Experience Program (August 2024) As an analyst on Mastercard’s Security Awareness Team, I was responsible for identifying and reporting security threats, such as phishing attacks. I analyzed areas within the business that required more robust security training and implemented training courses and procedures to address these needs.
Tata Cybersecurity Security Analyst Job Simulation (August 2024) In this simulation, I worked with Tata Consultancy Services on identity and access management (IAM). I gained expertise in IAM principles and cybersecurity best practices, ensuring strategic alignment with business objectives. I also delivered comprehensive documentation and presentations, showcasing my ability to communicate complex technical concepts effectively.
ANZ Australia Cyber Security Management Job Simulation (August 2024) This simulation involved identifying cybersecurity threats at ANZ. I investigated suspicious emails and analyzed packet capture files using open-source tools to detect and report potential threats.
Datacom Cybersecurity Job Simulation (August 2024) At Datacom, I focused on investigating a cyberattack and producing a detailed report with findings and recommendations to improve the client's cybersecurity posture. I also conducted a comprehensive risk assessment.
AIG Shields Up: Cybersecurity Virtual Experience Program (August 2024) I completed a threat analysis simulation for the Cyber Defense Unit, staying updated on CISA publications. My tasks included researching reported vulnerabilities, drafting clear guidance for teams on vulnerability remediation, and utilizing Python to write a script for ethical hacking, including bruteforcing decryption keys to avoid ransom payments.
Penetration Testing Project

My made up company for this project was Cyber Shield Solutions which was contracted to perform a penetration test for Near-Earth Broadcast Network (NBN) to identify and mitigate potential cybersecurity risks. The test focused on evaluating the security of NBN’s internet-facing web server and an internal network client machine using multiple VMs, including Kali Linux. Our methodology followed established frameworks such as OWASP and NIST, incorporating phases like reconnaissance, vulnerability scanning, exploitation, and privilege escalation. Tools such as NMAP, Nikto, ZAP, Nessus, Metasploit, SQLMap, and Burp Suite were utilized throughout the testing process. Significant issues were found, particularly on the web server, including critical flaws like anonymous FTP access and the use of outdated MD5 hashing. These weaknesses allowed us to gain unauthorized access, escalate privileges, and compromise sensitive data. The vulnerabilities identified pose a critical risk, and we have provided detailed recommendations for remediation to enhance NBN's cybersecurity defenses.Take a look below at the Pentest Report to see in-depth details.
MySQL Database Project
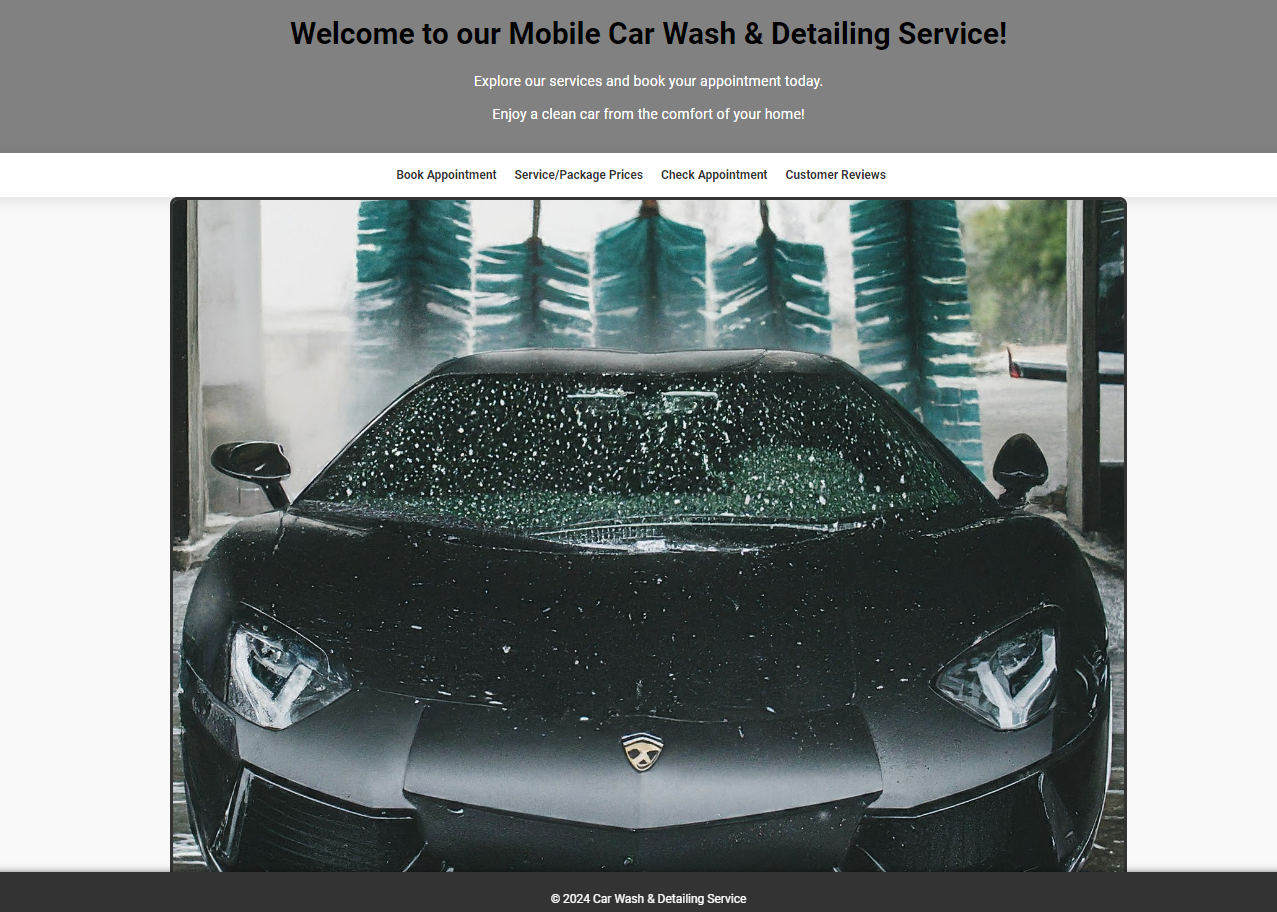
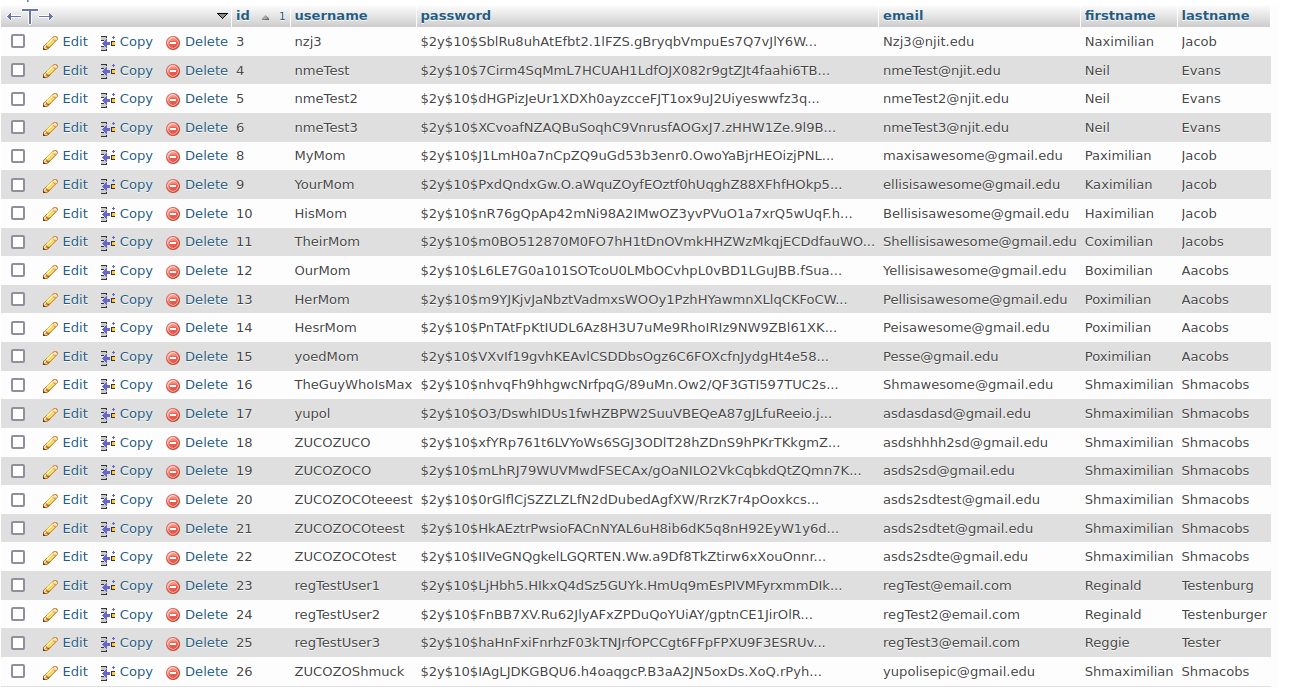
As part of my Database Systems Master Course at NYU, I was tasked to create a web application that showed a full working MySQL database. The database included 10 complex tables with primary keys, foreign keys, references, constraints, normalization, and integrity enforcement. Theres also Procedures, Views, Triggers, and Functions. My theme for the web application was a Mobile Car Wash and Detailing business where a customer can fill out a form to request a car wash or detail at their home or location of choice. Pricing is based on the car type, and size with various packages and services offered. Other parts of the website include customer reivews and adjusting employee wages based on ratings. Take a look at my web application below and the presentation slides for more info on this project.
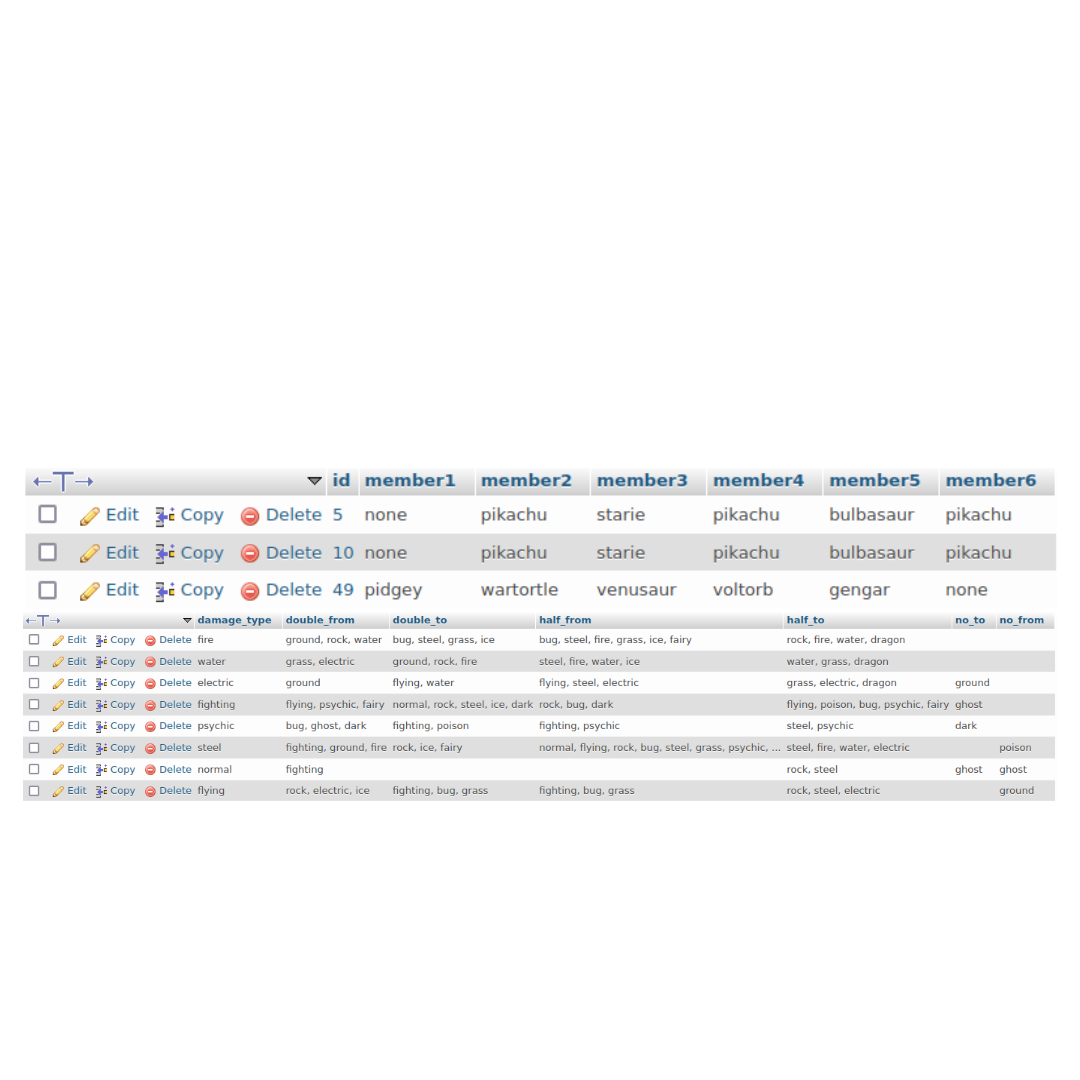
System Integration Project
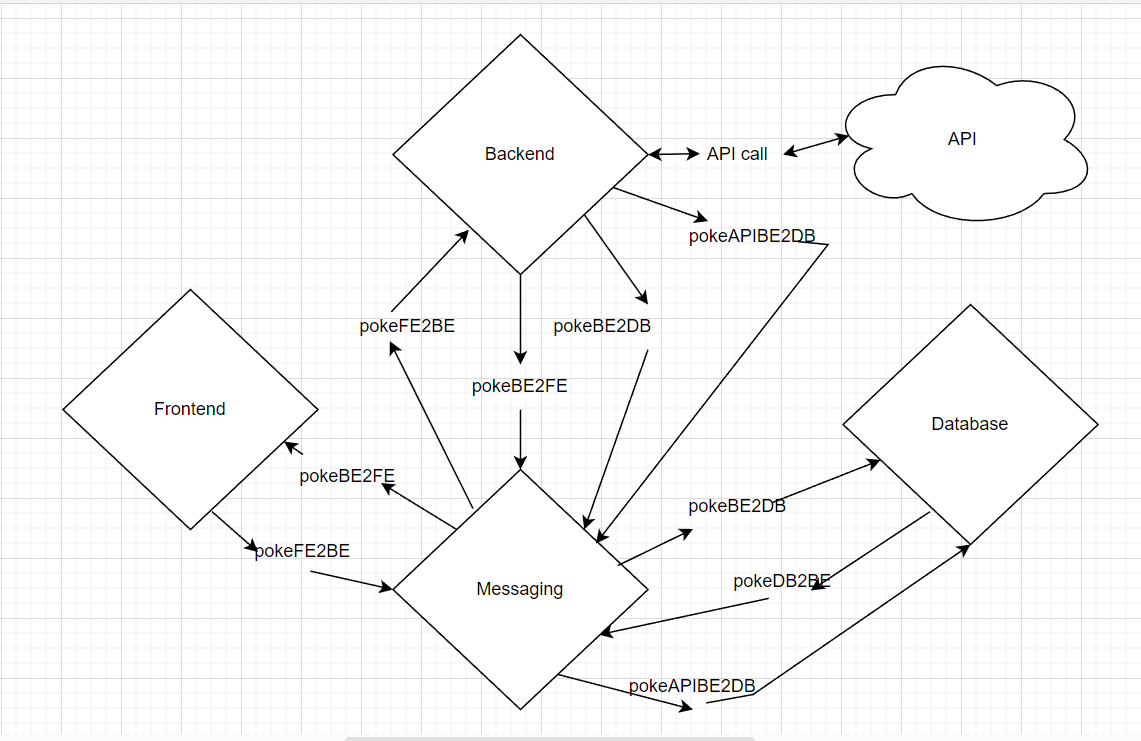
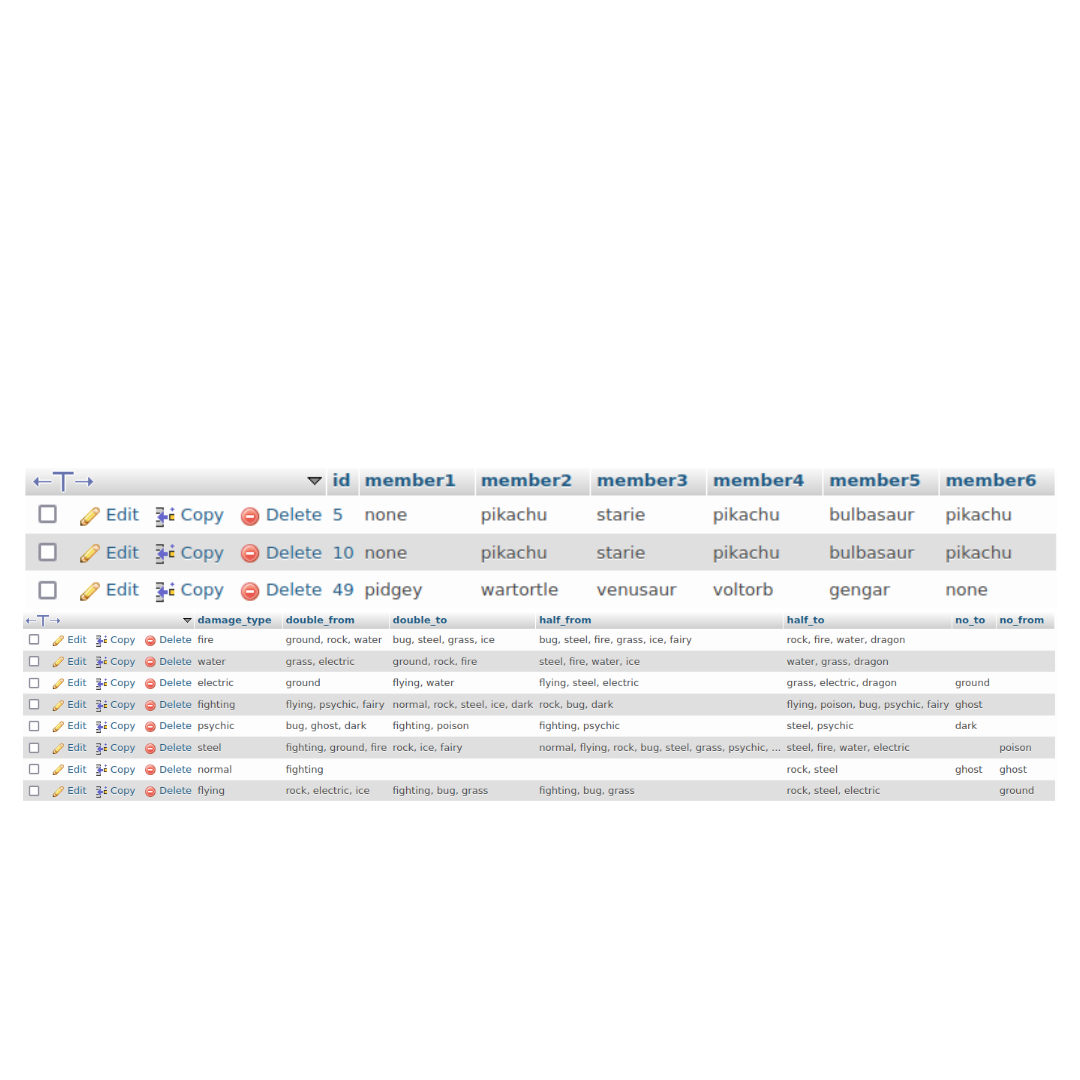
During my final year at the New Jersey Institute of Technology, I also worked on a Systems Integration Project
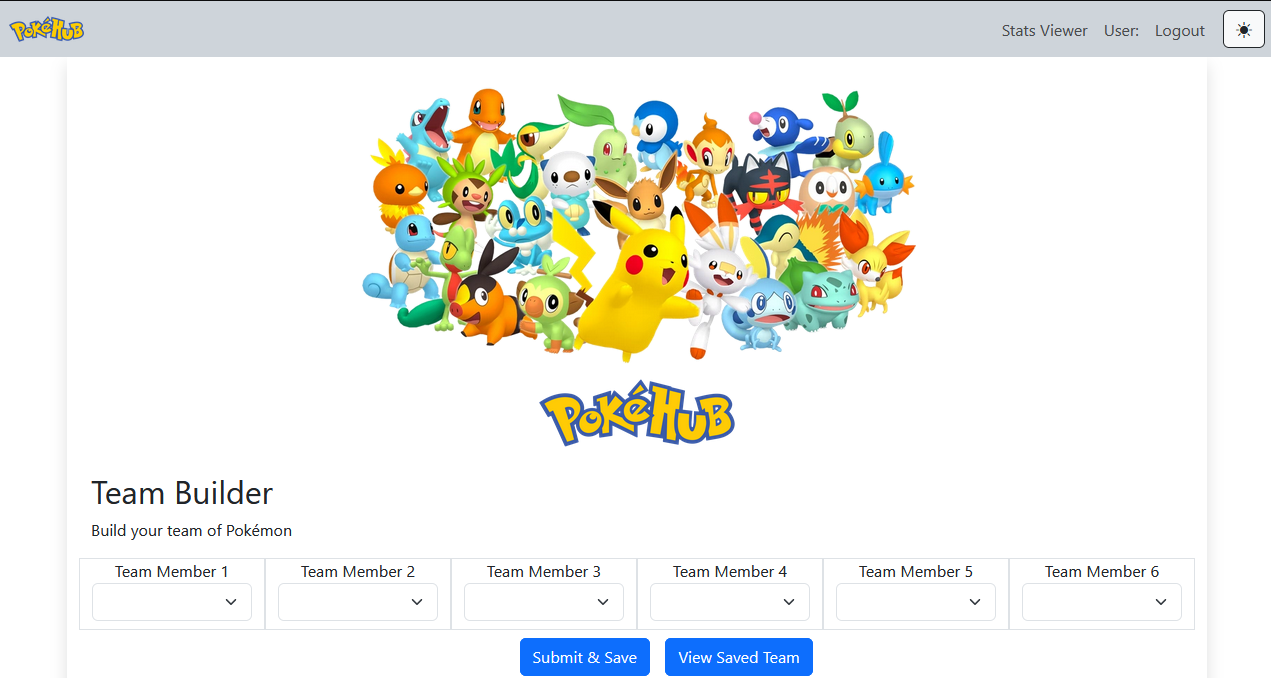
called PokéHub. The project aimed to provide Pokémon enthusiasts with a team-building application that enhances
their gaming experience. With this application, users can create and manage their optimized teams by utilizing
the vast collection of Pokémon and their stats, with the option of sharing them with other users. The project
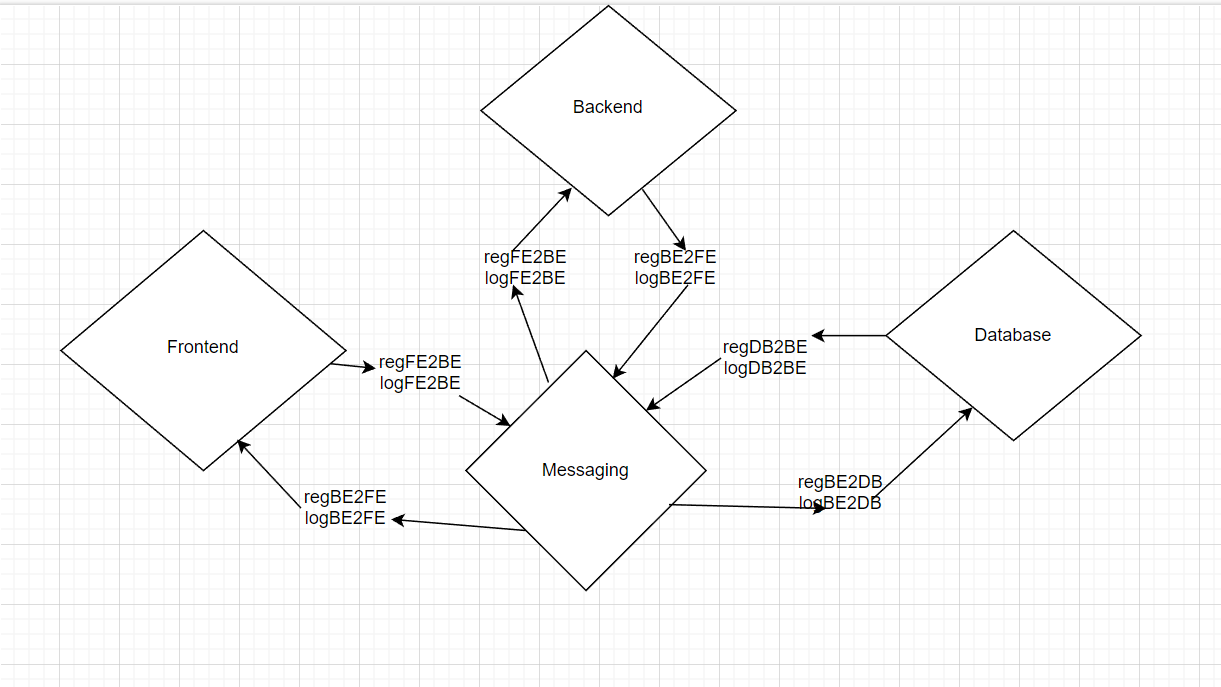
involved a robust system integration architecture consisting of a front-end instance, messaging instance,
database instance, and back-end instance. I played a key role in the development of the front-end instance,
ensuring an intuitive and responsive user interface. I also contributed to the integration of the messaging and
back-end instances, allowing for seamless team creation and management.
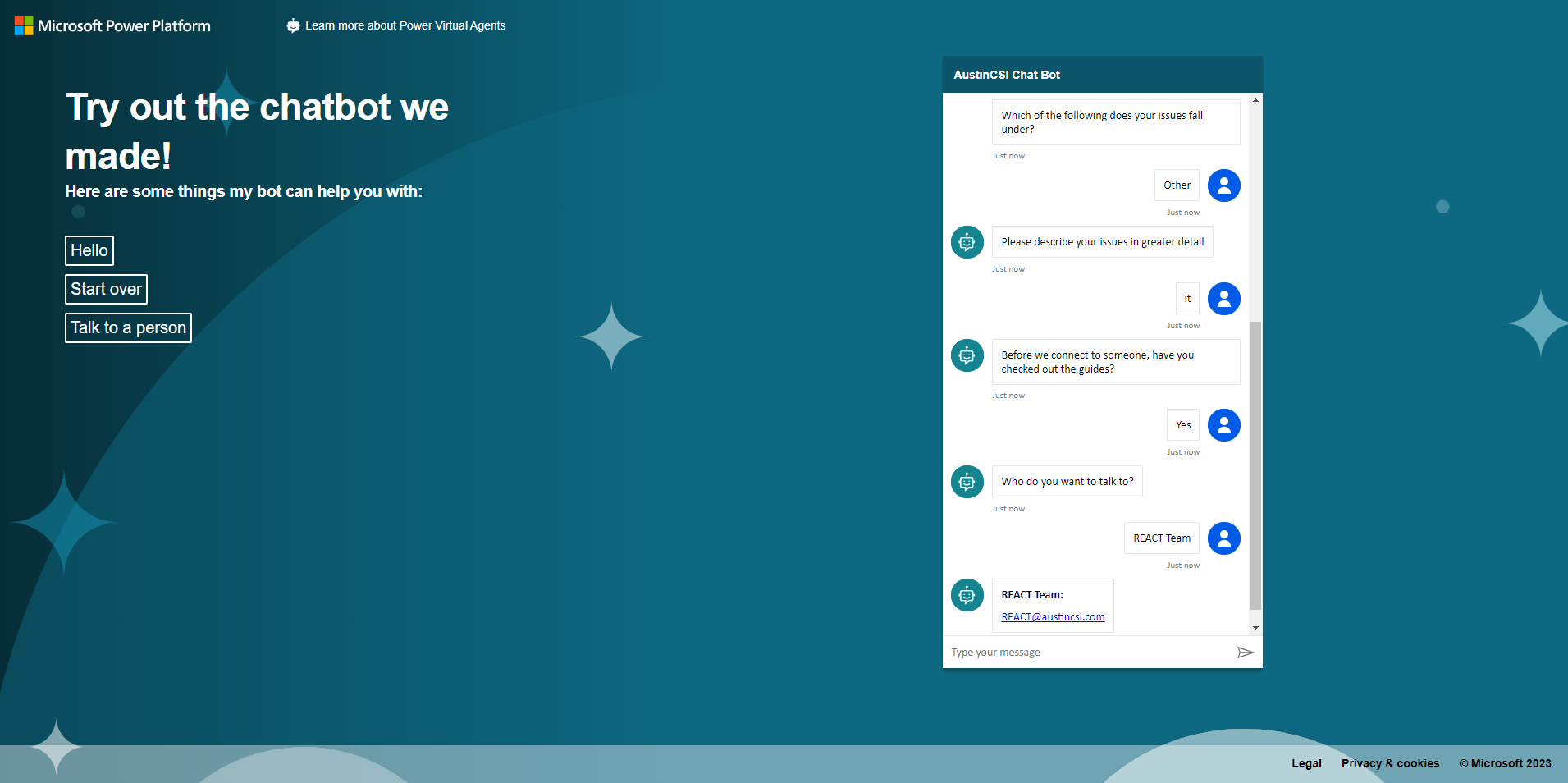
AustinCSI Hackathon Project
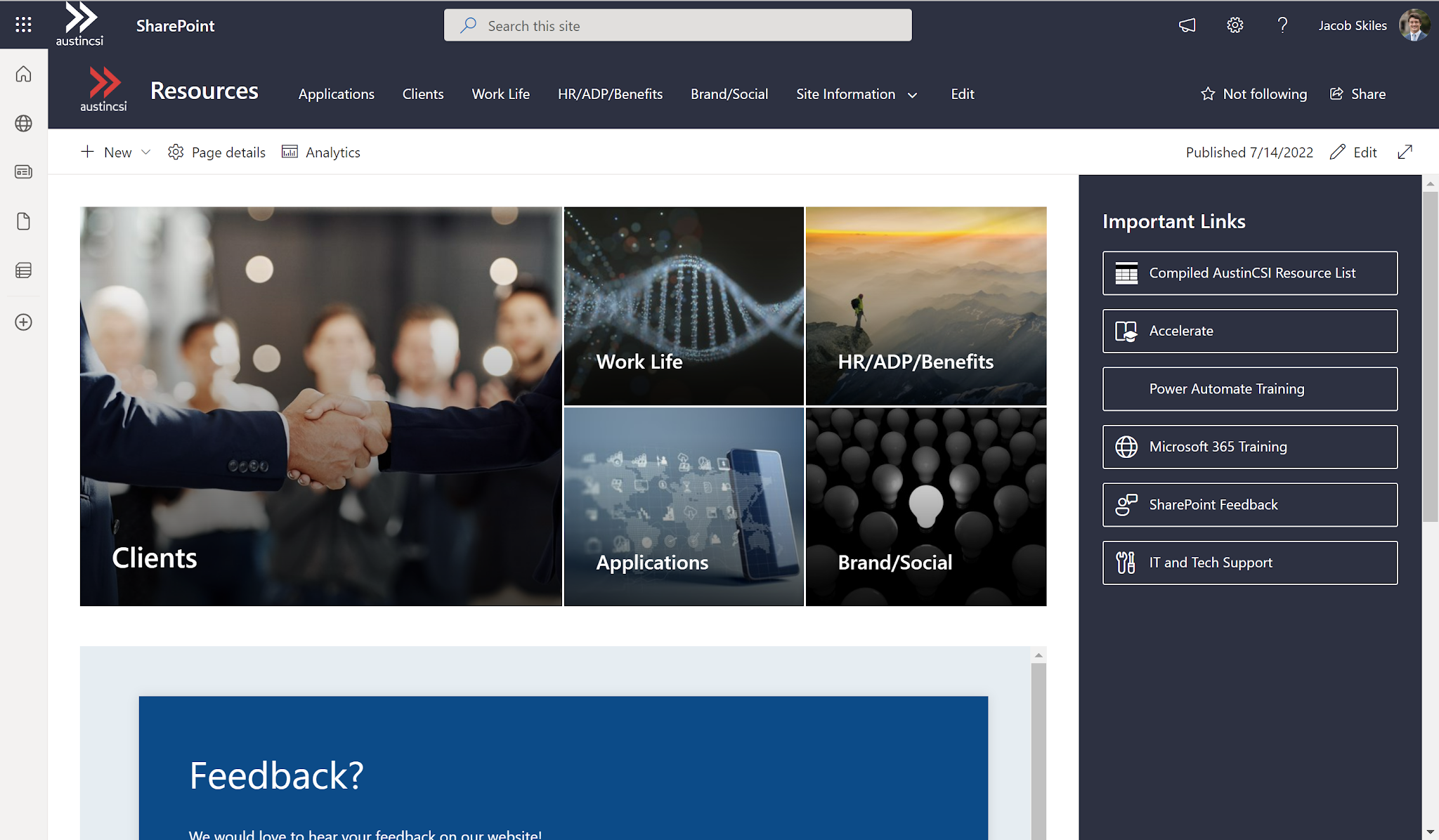
During my internship at AustinCSI, I worked on developing an AI chatbot for the company's new intranet
SharePoint site, called The Source. The objective of the project was to create a user-friendly tool that would
assist new employees in navigating the available resources more easily. To accomplish this, I utilized Microsoft
Power Apps, specifically Power Automate, to build the AI chatbot.
The motivation behind the project stemmed from the challenges faced by consultants at AustinCSI when accessing
resources. Existing resources were scattered across multiple platforms, leading to inconsistency and
difficulties in locating the necessary information. Consultants often wasted time searching for resources or
were unaware of the resources available to them.
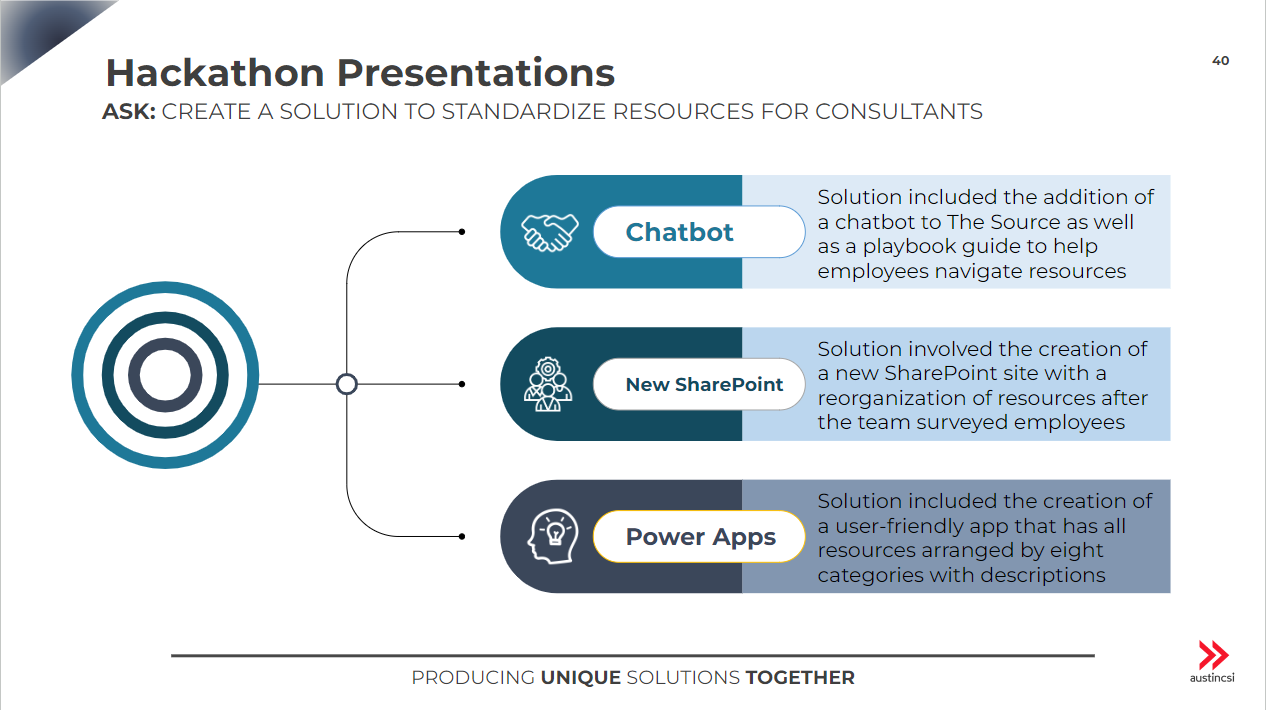
To address these issues, the company requested the development of a solution that would establish a simple and
unified method for all AustinCSI consultants to search and access existing resources quickly. The proposed
solution consisted of integrating a chatbot into The Source and providing a playbook guide to aid employees in
navigating the available resources.
The chatbot was strategically positioned within The Source to assist users in finding the specific information
they required. By leveraging the capabilities of Microsoft Power Apps, particularly Power Automate, I developed
a chatbot that could understand user queries and direct them to the relevant resources. This streamlined the
process and eliminated the need for consultants to manually search for resources, saving them time and effort.
In addition to the chatbot, a playbook guide was created to provide employees with step-by-step instructions on
how to navigate the available resources effectively. This guide served as a supplementary tool to assist users
in familiarizing themselves with The Source and maximizing its potential.
Overall, the project aimed to enhance the user experience of AustinCSI consultants by simplifying resource
access and navigation. By integrating an AI chatbot into The Source and providing a playbook guide, the project
successfully addressed the challenge of scattered and inconsistent resources, empowering consultants to find the
information they need efficiently.
Cisco Capstone Project
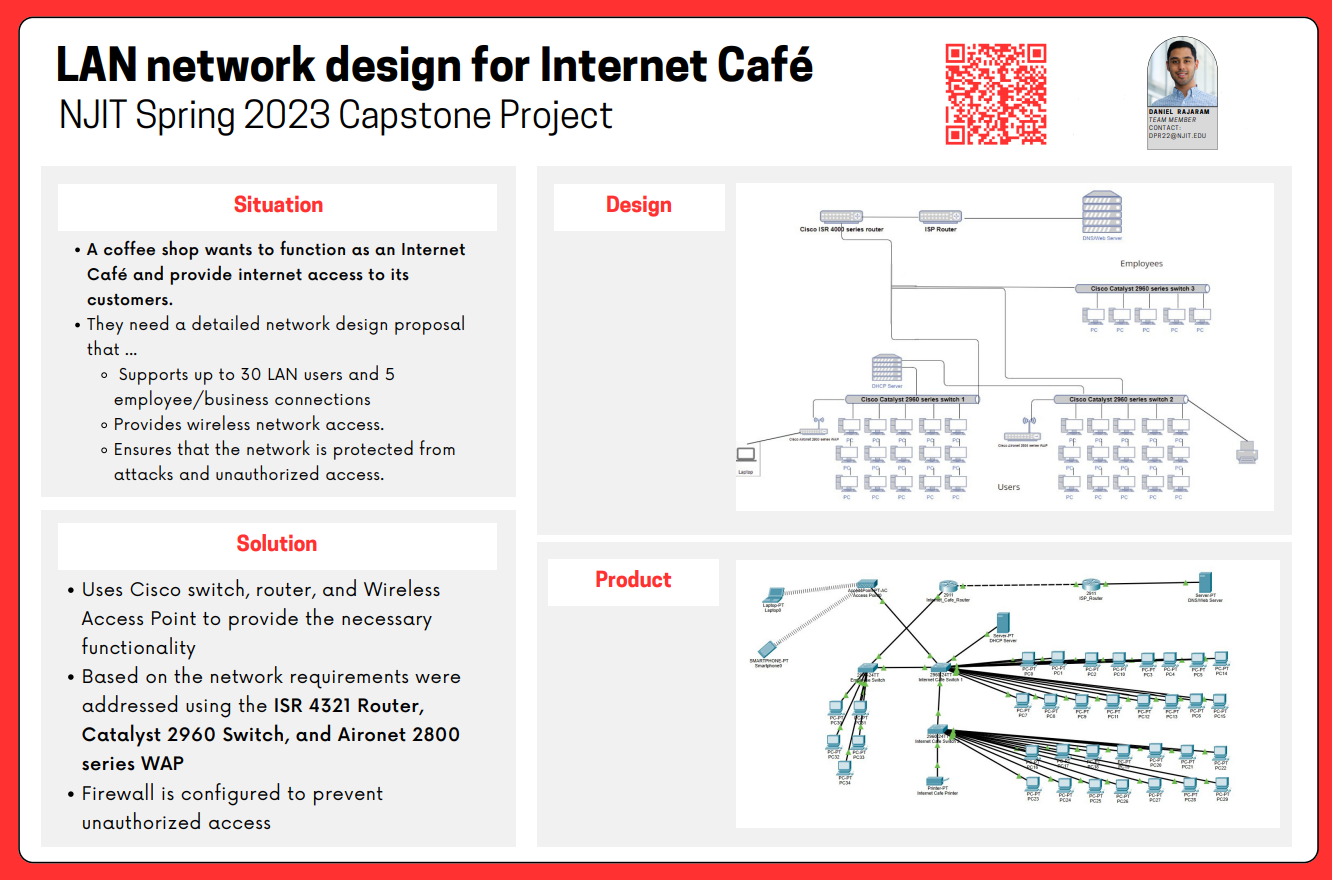
This project involves the design/configuration of a LAN network for an internet cafe. The project aims to provide reliable and secure wireless network access for customers and employees while considering scalability, budget constraints, and network security, through Cisco Packet tracer.
Other Projects/Presenations